Integral Bytes Blog
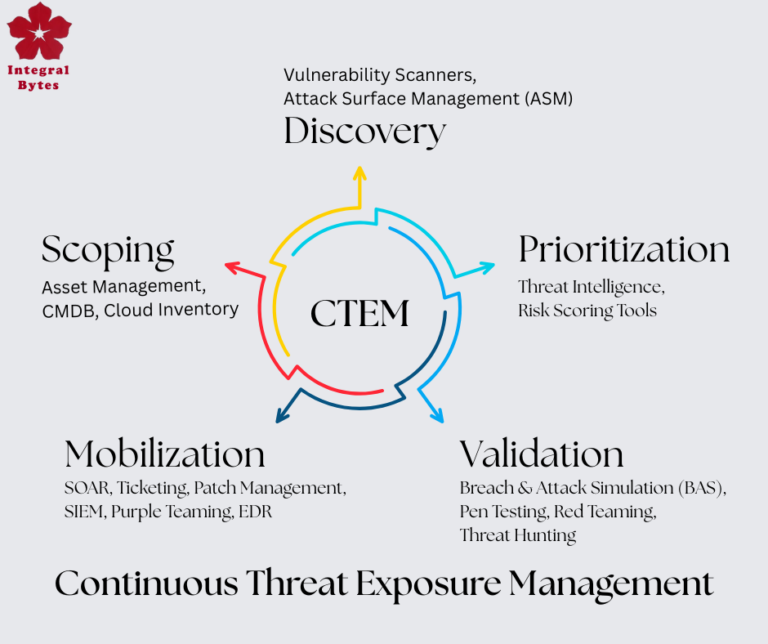
CTEM (Continuous Threat Exposure Management) is extremely important for a CISO (Chief Information Security Officer) — not just as a technical practice, but as a strategic framework that supports the...
Sigma rule creation plays a key role in Continuous Threat Exposure Management (CTEM) by helping organizations detect and respond to threats more efficiently and proactively. Sigma Rules Sigma is a...
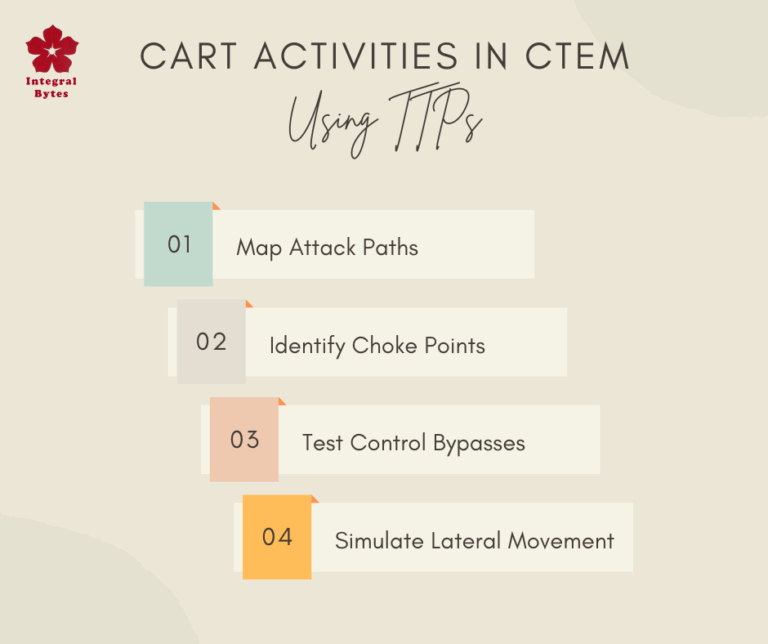
CART CART stands for Continuous Automated Red Teaming.It’s a key component in CTEM (Continuous Threat Exposure Management), which is a proactive cybersecurity strategy focused on continuously...
Well. CTEM or Continuous Threat Exposure Management is an evolving framework, not a rigid set of technology! When we search for CTEM solutions, we find many, each claiming to be CTEM and when we dig...
There are a few good certifications available on net and you can try. Some are free, some need small payment. Google CyberSecurity...
Here are a few relevant postings for freshers, discovered on LinkedIN Jobs and Naukri. Deloitte: AppSec & VA PT https://www.linkedin.com/jobs/view/3942092733...
- 1
- 2